Understanding How To Reset End To End Encrypted Data
In an increasingly digital world, the importance of data privacy cannot be overstated. Users are becoming more aware of the need to protect their personal information, leading to a rise in the use of end-to-end encryption. However, as with any technology, there may come a time when you need to reset end to end encrypted data. This process can seem daunting, but it is essential to understand the implications and the steps involved. When we talk about resetting end-to-end encrypted data, we are referring to the ability to restore or delete information that has been secured through encryption methods. This can be necessary in a variety of scenarios, such as when a user switches devices, needs to recover lost data, or wishes to clear their history for security reasons.
As we delve deeper into the topic, we'll explore the various aspects of resetting end-to-end encrypted data, including the reasons one might need to do so, the potential risks involved, and the steps to ensure that the process is smooth and effective. With the right knowledge and tools, users can manage their encrypted data effectively, ensuring both security and accessibility.
In this article, we will provide a comprehensive guide to resetting end-to-end encrypted data, answering common questions and offering practical advice. Whether you're a tech novice or an experienced user, understanding this process is crucial in today's privacy-centric world.
- Unveiling The Mystique Of The Blue Alien From The Fifth Element
- Swear Words In Sign Language Understanding And Respecting The Art Of Communication
What is End-to-End Encryption?
End-to-end encryption (E2EE) is a method of data transmission where only the communicating users can read the messages. In this system, the data is encrypted on the sender's device and only decrypted on the recipient's device, ensuring that no intermediaries can access the information. This is particularly important for protecting sensitive data such as personal messages, financial information, and confidential work documents.
How Does End-to-End Encryption Work?
The process of end-to-end encryption relies on encryption algorithms and keys. When a user sends a message, it is encrypted using a unique key, which is only accessible to the recipient. This means even if the data is intercepted during transmission, it remains unreadable without the proper decryption key. Most messaging platforms that utilize E2EE, such as WhatsApp and Signal, ensure that only the sender and intended recipient can view the content of their conversations.
Why Do You Need to Reset End to End Encrypted Data?
There are several reasons why you might need to reset end-to-end encrypted data:
- Switching Devices: When upgrading to a new device, you may want to transfer or wipe your encrypted data.
- Data Recovery: If you lost access to your encrypted data, resetting it can help restore your information.
- Security Concerns: If you suspect your data has been compromised, resetting is a proactive way to protect your information.
- Clear History: For privacy reasons, you may want to delete old conversations and data.
What Are the Risks of Resetting End to End Encrypted Data?
Although resetting end-to-end encrypted data can be beneficial, it also comes with risks. One significant risk is the potential loss of data that may not be recoverable once deleted. Additionally, improperly resetting encrypted data can leave vulnerabilities, allowing unauthorized access. Therefore, understanding the process and taking the correct precautions is vital.
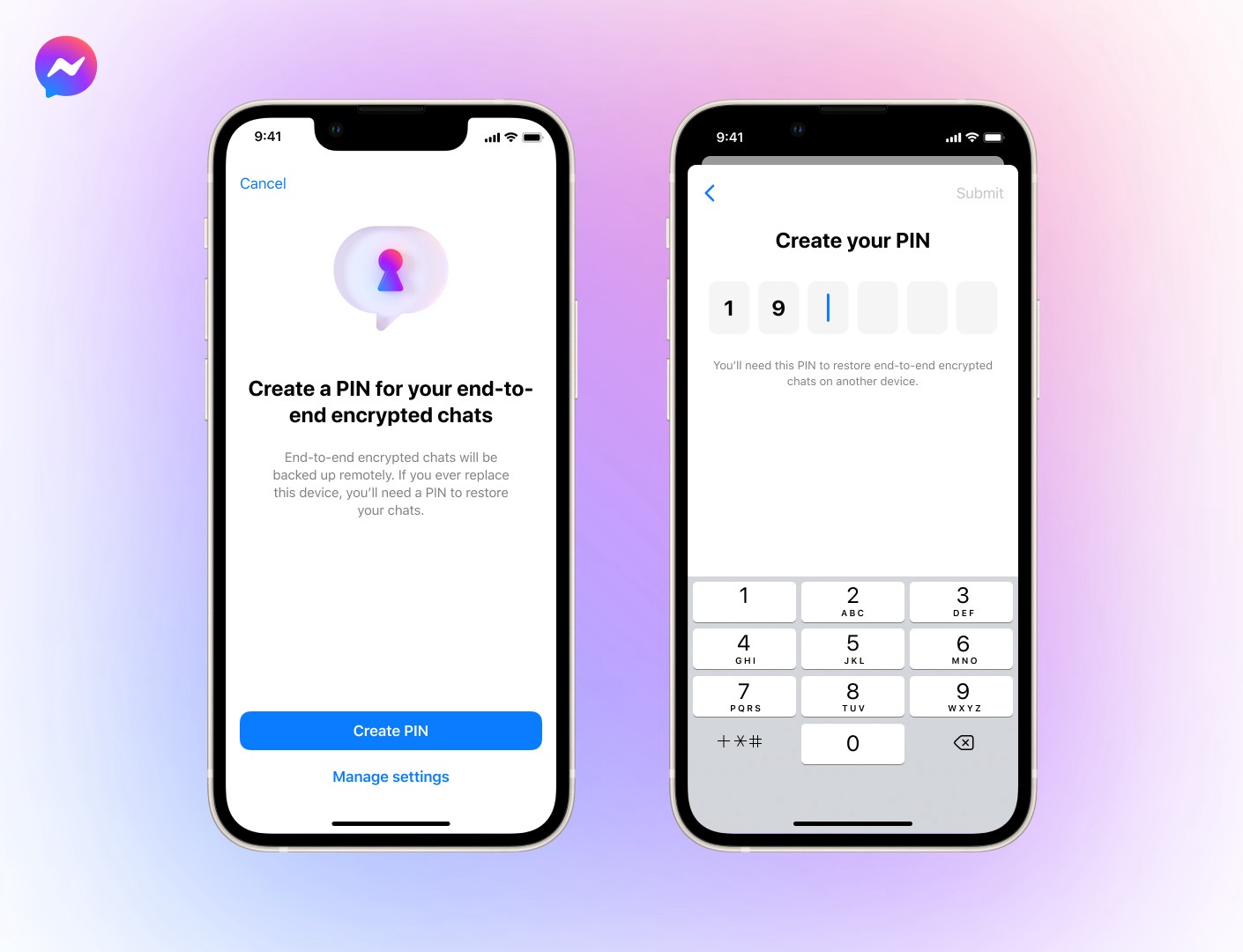
How to Safely Reset End to End Encrypted Data?
To reset end-to-end encrypted data effectively, follow these steps:
- Backup Your Data: Before proceeding with any reset, ensure you have a secure backup of your important data.
- Access the Settings: Navigate to the settings of your messaging or data storage application.
- Find the Reset Option: Look for the option to reset or clear data, which is often located under security or privacy settings.
- Follow the Prompts: Carefully follow the prompts provided by the application to reset your data.
- Verify the Reset: Once completed, verify that the reset was successful and that your data is no longer accessible.
Can You Recover Data After Resetting End to End Encrypted Data?
Recovering data after it has been reset can be challenging. In many cases, if you did not create a backup prior to the reset, the data may be permanently lost. Some applications offer recovery options, but this often depends on the specific software being used. If recovery is crucial, consult the application’s support resources for guidance.
Conclusion: Mastering the Reset of End to End Encrypted Data
Understanding how to reset end-to-end encrypted data is a vital skill in today’s digital landscape. Whether you are switching devices, worried about security, or simply want to clear your data history, knowing the proper steps to reset this type of data can help you maintain control over your privacy and information. By being informed and cautious, you can safely navigate the complexities of encrypted data management.


Detail Author:
- Name : Aleen Berge
- Username : nharvey
- Email : carol.schmitt@bernier.com
- Birthdate : 1985-04-23
- Address : 91542 Roberts Mews Suite 907 New Emelieburgh, KS 49877-3212
- Phone : 619.441.5985
- Company : Herman-Dietrich
- Job : Forester
- Bio : Et aut qui ipsum. Asperiores aliquam dignissimos voluptatum quibusdam itaque.
Socials
linkedin:
- url : https://linkedin.com/in/nicholas1867
- username : nicholas1867
- bio : Dolorem aut fuga non voluptatibus accusamus quia.
- followers : 118
- following : 19
instagram:
- url : https://instagram.com/hilln
- username : hilln
- bio : Unde at ex molestiae. Dolor ab culpa et aspernatur aut temporibus. Vel officiis sed quam voluptate.
- followers : 1704
- following : 2287
tiktok:
- url : https://tiktok.com/@nicholas_hill
- username : nicholas_hill
- bio : Fuga sed et delectus. Explicabo similique non veniam assumenda molestiae.
- followers : 347
- following : 325
facebook:
- url : https://facebook.com/hilln
- username : hilln
- bio : Molestiae quia non voluptates nihil minima consequuntur.
- followers : 1947
- following : 570
twitter:
- url : https://twitter.com/nicholas_dev
- username : nicholas_dev
- bio : Laboriosam commodi fugit molestiae quidem totam. Nemo illo quia repudiandae est. Quia eos sunt deserunt quis id porro deserunt dolore.
- followers : 519
- following : 2723